Bridge Network
When you run a container without specifying a network, it is connected to the default bridge network. Docker then assigns an internal IP address to the container, and all containers on the same bridge network can communicate via this internal IP.
The concept is very similar to how NAT works for a router/firewall. Anything within the bridge network is considered "private" to the docker host, When you define a port mapping for a container, you are "opening up a port" on the docker host, to allow traffic from the outside to the container.
For example, in the following diagram, all the containers are on a bridge network, and recieves an internal IP. Because each container is on the same bridge network, they are talk to each other via their internal, conatiner IP.
One container (172.17.17.1) setup with a port mapping, mapping the container's port 8443 to the docker host's port 443. This allows the allowing traffic from conatiner's port 8443 to exit the docker containment, and onto the docker host's port 443.
When an traffic rquest comes in from the outside (192.168.1.101) to the docker host (192.168.1.100), at port 443, the docker engine will see that there is an port mapping for 443 to one of the container, and "NAT" the traffic request.
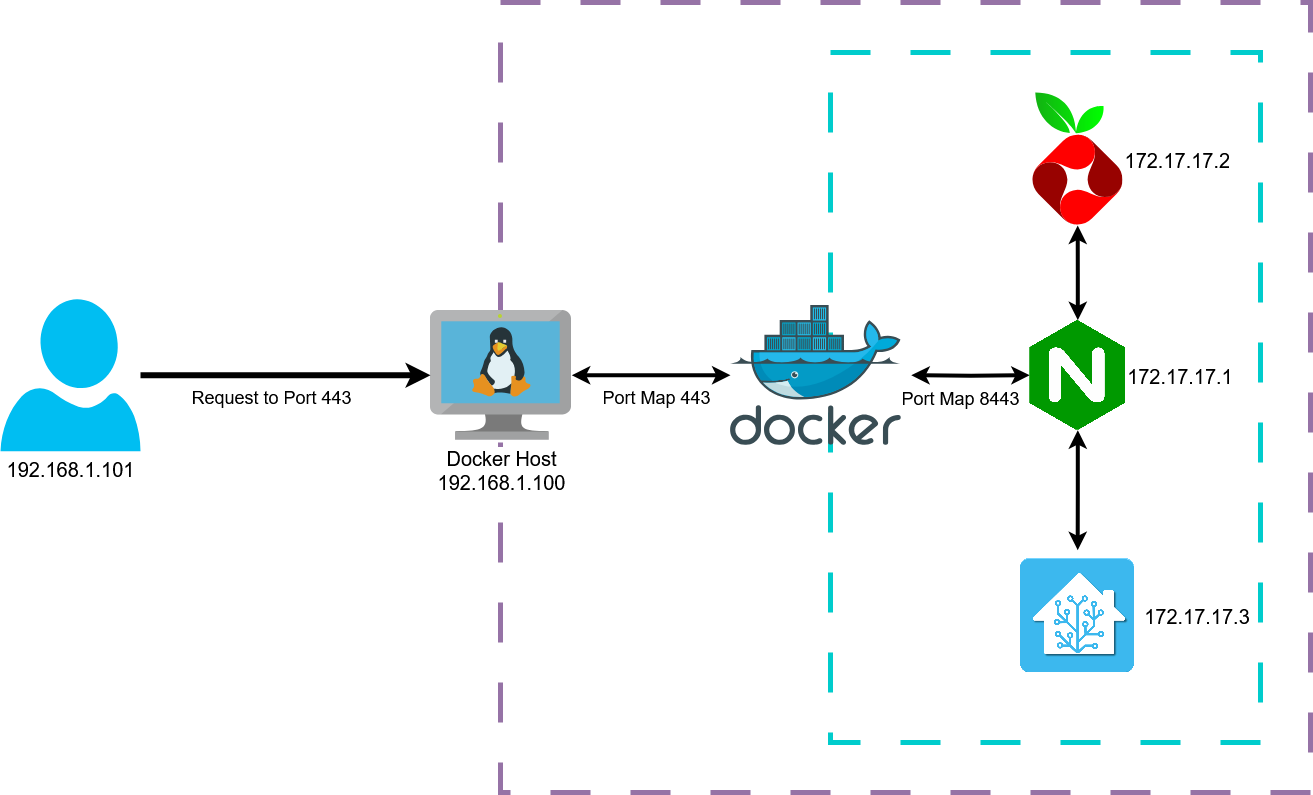
This type of networking is very useful when you want to expose multiple containers behind a reverse proxy container like NGINX. Simply place all the containers on the same default bridge network, and then port map only the NGINX container.